Edgewatch Port Scan is a powerful network scanning tool designed to help users identify open, closed, or filtered ports on a network. Mirroring the capabilities of Nmap, it provides detailed insights into network configurations by scanning a variety of protocols, including TCP, UDP, and SCTP. This helps organizations assess vulnerabilities by identifying entry points that could be exploited. Whether you are checking for open services, security compliance, or diagnosing network issues, Edgewatch Port Scan offers speed, flexibility, and deep scan customization options, allowing scans to be tailored to specific needs. Features include OS detection, version identification, and service discovery, which assist security professionals in creating a full network fingerprint for improved security posture.
Edgewatch Port Scan also includes advanced scanning techniques such as SYN, ACK, FIN, and NULL scans, offering the flexibility to perform comprehensive reconnaissance without triggering alerts on the target system’s intrusion detection systems (IDS). It can adjust scan intensity, utilize different timing templates to optimize network load during scans, and include features to handle the complexities of large networks. This level of detail makes Edgewatch Port Scan an indispensable tool for penetration testers, system administrators, and security analysts. In network security, understanding port status is vital to identifying potential vulnerabilities that attackers could exploit. Ports are the communication endpoints for network services, and their statuses—open, closed, or filtered—determine whether a service is accessible. Open ports are particularly critical because they indicate an active service on the target machine, which could potentially be exploited if misconfigured or outdated.
On the other hand, closed ports are not currently in use, but still respond to probes, which can provide useful information to attackers. Filtered ports are shielded from direct access, often by a firewall, making it more difficult for attackers to gather information.Knowing the status of network ports is essential for security because it helps organizations ensure that only necessary ports are exposed, reducing the attack surface. Regular port scanning, such as with Edgewatch Port Scan, allows teams to audit and harden their network by closing unnecessary ports and securing critical services, which is key to maintaining robust cybersecurity defenses.
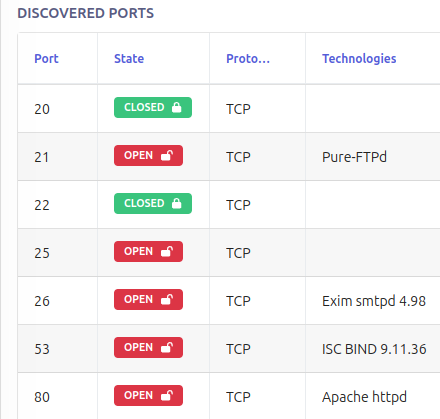
Open Ports
Open ports are actively accepting incoming connections, meaning they are associated with a service or application that is running and ready to communicate. These are essential for network operations, allowing legitimate traffic through; however, they also present potential security risks. If not properly configured or monitored, open ports can be exploited by attackers to gain unauthorized access or deliver malicious payloads. It is crucial to ensure that only necessary ports are open and that all associated services are secured with strong authentication and up-to-date patches.
Closed Ports
Closed ports indicate that no service is currently listening on that port, but the port is still accessible, responding to scanning attempts with a message like “port closed” or sending a TCP RST packet. Although they do not pose a direct threat, closed ports still provide useful information about the system’s configuration and network presence to potential attackers. For this reason, security teams often recommend using firewalls to prevent closed ports from responding to scans, further reducing the exposure of network information.
Filtered Ports
Filtered ports are shielded from direct communication by a firewall or other network security device, which blocks the port from responding to scanning attempts. This leaves the scanner unable to determine whether the port is open or closed. Filtered ports are a sign of robust network defenses, making it harder for attackers to gather intelligence on the system. However, improperly configured firewalls may still leave filtered ports vulnerable to bypassing techniques, so regular review of firewall rules is necessary to ensure that filtered ports remain secure.
Unfiltered Ports
Unfiltered ports respond to scan probes but the scanner cannot determine whether they are open or closed. These ports are uncommon in typical environments because their behavior provides limited security information. Unfiltered ports require further scrutiny because they may still reveal useful data to an attacker. While they do not offer a direct indication of a service running, unfiltered ports can suggest that further investigation is needed to assess the network’s security posture.
Open|Filtered Ports
Ports marked as open|filtered indicate that the scanner cannot definitively determine whether the port is open or filtered. This often occurs when a firewall or security device is in place, partially filtering traffic but allowing some communication to pass through. From a security perspective, open|filtered ports require close attention since they could be actively used by services that may be susceptible to attack, yet the exact nature of their openness is unclear due to filtering.
Closed|Filtered Ports
Closed|filtered ports represent a scenario where a scanner cannot distinguish if a port is closed or filtered by a firewall. This uncertainty makes it difficult for attackers to infer whether a service exists behind the port or whether it is simply being blocked by security measures. From a defensive standpoint, maintaining closed|filtered ports adds a layer of ambiguity to network scans, which can help prevent attackers from accurately mapping the network’s layout and defenses.
By utilizing Edgewatch Port Scan, organizations can gain real-time insights into the state of their network ports and take proactive measures to secure their systems from potential threats.