Automate protection and mitigate risk to the extent of your internet exposure
The Edgewatch Attack Surface Management Platform offers a unique perspective, enabling you to see your external attack surface as a hacker does. Utilizing advanced bot technologies akin to those employed by threat actors, the platform’s discovery engine meticulously scans every connection, link, embedded code, and DNS reference. This comprehensive scanning builds a detailed outside-in view of your organization’s public-facing digital footprint. The platform provides continuous vulnerability management and penetration testing, enhancing security visibility and intelligence.
Our fully extensible API provides users with the ability to integrate EdgeWatch vulnerability intelligence into any GRC or bug tracking system.
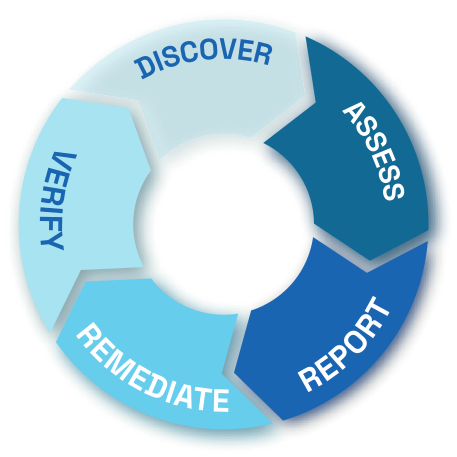
Its ongoing process of discovery, assessment, reporting, and protection covers your entire attack surface. This relentless vigilance equips security teams with the necessary awareness and tools to effectively safeguard the enterprise against evolving cyber threats. By staying ahead in identifying potential vulnerabilities, Edgewatch ensures that your organization can preemptively address security issues, maintain a robust defense posture, and adapt to the ever-changing landscape of digital security.
Assessment & prioritzation
Edgewatch’s intelligent vulnerability assessment engine evaluates assets not just by type but also by their organizational context. Using a proprietary, multi-layered approach, it assesses vulnerabilities for risk and exploitability based on unique security intelligence. This strategy minimizes false positives and provides crucial insights, helping teams prioritize the most significant threats for immediate action.
Reduce your external attack surface
In today’s dynamic and dispersed enterprise environments, complete visibility over the attack surface is crucial for protection. Continuous audits and assessments of vendors’ security postures are vital for effective security. Minimizing vulnerabilities involves reducing the number of assets prone to them. Decommissioning unnecessary operational assets can significantly reduce the overall attack surface, thereby enhancing defense capabilities.
Insights and active protection
Edgewatch Attack Surface Management Platform provides your team with suggested steps to mitigate or remediate complex vulnerabilities to accelerate MTR. For additional peace of mind, our platform’s Active Protection feature provides automated defense from breaches interacting feeding your Firewalls.
Risk Assesment
Our vulnerability assessment engine continuously identifies, ranks, and prioritizes vulnerabilities, aiding decision-makers in formulating effective risk responses. Edgewatch evaluates the likelihood of business vulnerabilities to cyberattacks, using key indicators and risk signals for a strategic view of threats. This approach helps in identifying and minimizing, or even eliminating, potential damage to the organization.
Attack prevention
Edgewatch helps prevent brand damage, data breaches, and financial losses by providing a clear list of action items and a streamlined workflow, enabling security teams to address critical issues proactively. It offers full visibility of the external attack surface, allowing informed decisions on maintaining, mitigating, or removing elements to reduce exposure to risks. This approach ensures prioritization of the most pressing vulnerabilities, safeguarding the organization effectively.
Digital Supply Chain coverage
Your digital security is only as good as your partners’ digital security. Inline APIs, third party libraries or code dependencies, your IT vendors, manufacturers, suppliers, or service providers all pose some risk to your network. A business-stopping supply chain incident is only a few clicks away.
Edgewatch Walkthrough
Feel like navigating the vast digital universe of your company’s assets is a space odyssey? Our latest infographic video demystifies this journey! With EdgeWatch, you’ll not only map out your enterprise IT cosmos but also uncover every internet-facing asset and their cosmic connections. Plus, our multilayered vulnerability assessment engine constantly guards your digital space!
Get ready to launch with EdgeWatch and transform your security strategy into an interstellar adventure!
How Edgewatch Attack Surface Management Platform Works
Edgewatch’s continuous process of discovery, assessment, reporting, and protection across your entire attack surface
provides the necessary awareness for security teams to effectively protect the enterprise.