What We Do
Edgewatch Risk & Attack Surface Management Platform assists companies in
discovering, monitoring, and analysing their digital footprint.
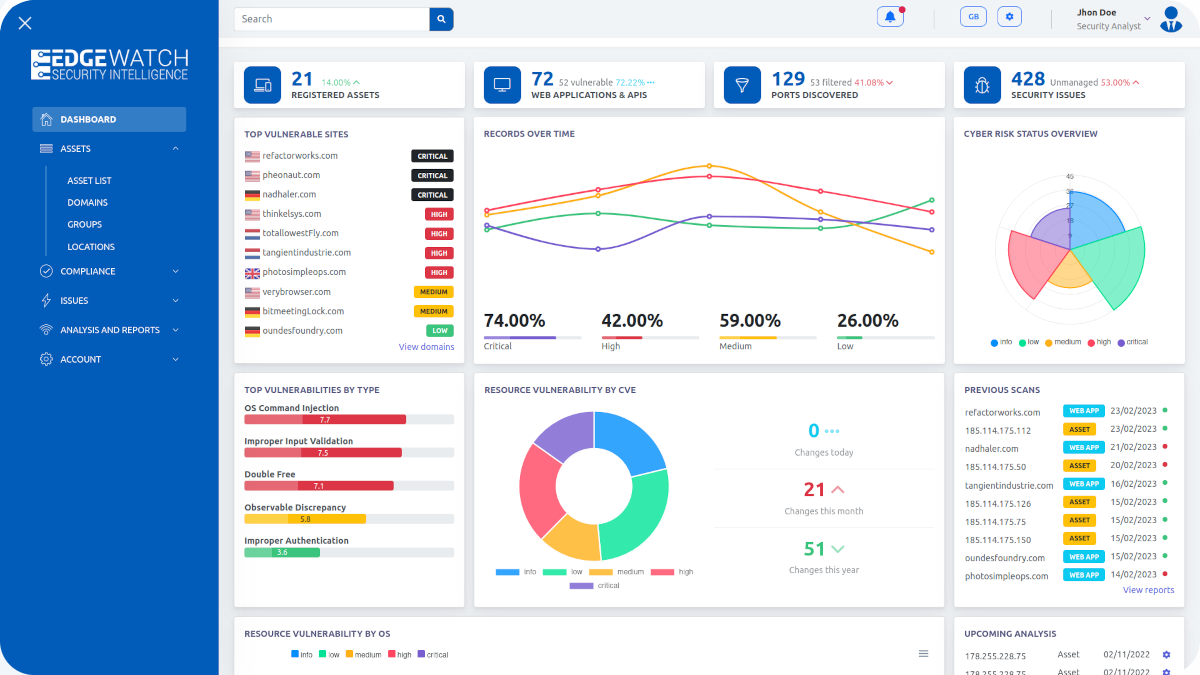
Exposure Insights
View a comprehensive summary of asset discovery including scans, organizational ASM/EASM/SET assessments, discovered assets, vulnerabilities, and data breaches.
Assets Analysis
Examine the impact on each asset with a detailed inventory, including ASN, IP blocks, and addresses. Mark false positives or archive, and assess the associated risks.
Breach intelligence
Access data breach information from open sources and the dark web, revealing affected users and internal users with compromised credentials.
Vulnerability Sorting
Contextualize findings to manage vulnerabilities effectively by categorizing assets like organizations, subsidiaries, domains, and more.
False Positive Filtering
Navigate through alerts efficiently by marking non-relevant findings as false positives or archive them for record-keeping.
Risk Evaluation
Analyze vulnerabilities and assess risks with precision to understand the security stance and prioritize responses.

Unlocking Proactive Security through Risk & External Attack Surface Management
Fortifying Cyber Defense
Edgewatch provides comprehensive visibility into an organization’s attack surface, enabling proactive identification and management of potential vulnerabilities. It helps to ensure that security measures are not just reactive but preemptively aligned with the threat landscape..
Comprehensive Visibility
Edgewatch offers a bird’s-eye view of an organization’s digital presence, pinpointing vulnerabilities before they can be exploited by attackers.
Proactive Protection
By identifying exposed assets and associated risks, Edgewatch allows businesses to take proactive steps in strengthening their security posture.
Dark Web Insights
Edgewatch delve into the depths of the internet, including the dark web, to uncover and alert organizations about compromised credentials and data breaches.
Do you have any question?
Feel free to contact us anytime.
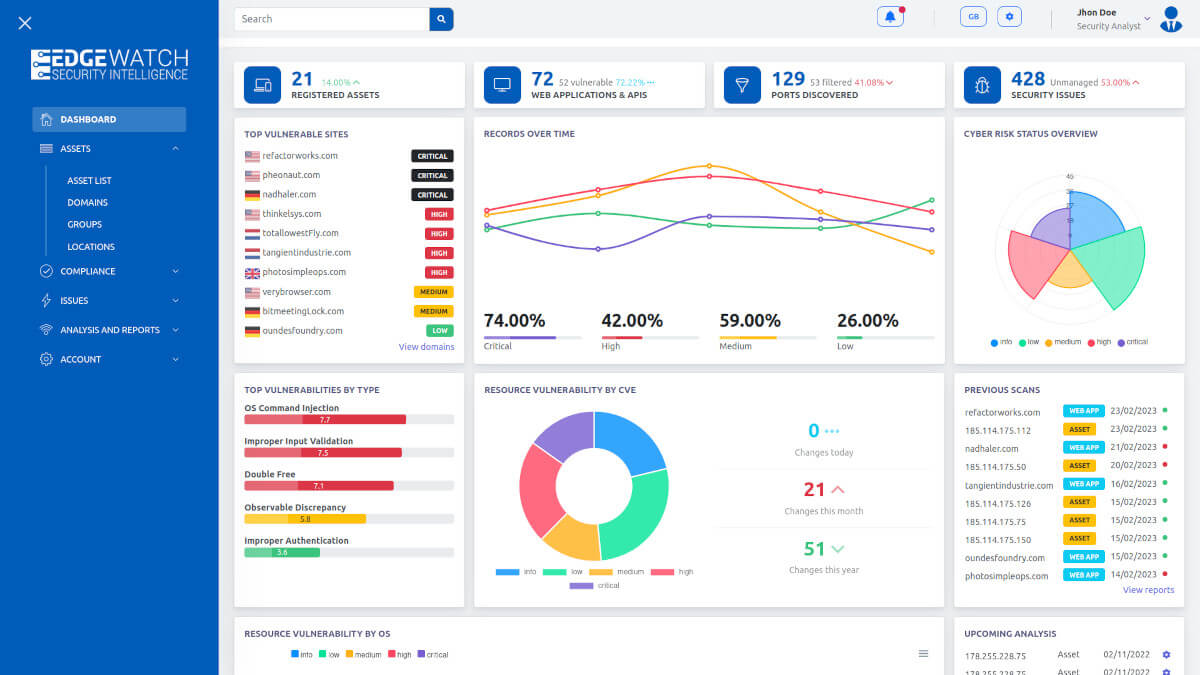
Scratch Beyond the Surface
Discover a suite of advanced features designed for proactive discover, offering deep visibility, integrated intelligence, and a responsive security ecosystem to safeguard your digital frontier effectively.
Could you enumerate how many servers or IT services your company owns?
We took to the streets with our burning question. Guess what we uncovered? Check out the video!