Edgewatch Platform Features
Attack surface monitoring
Find out what you have exposed to the internet, and restrict anything that doesn’t need to be there.
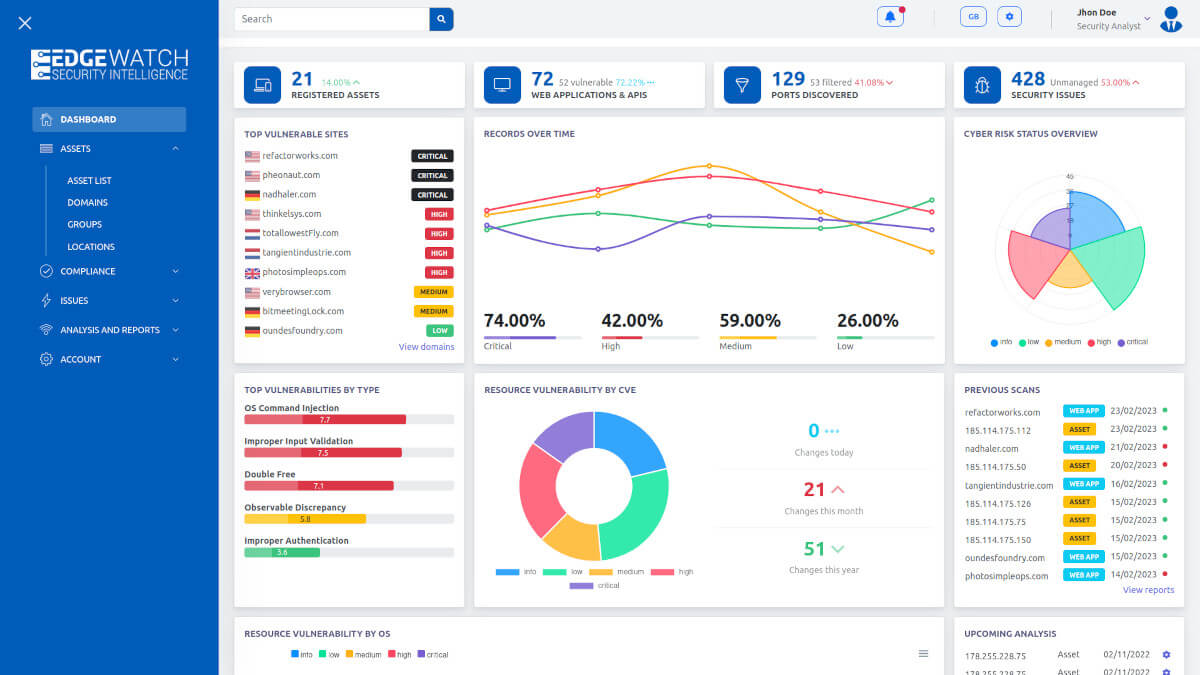
Attack Surface Monitoring
With our Attack Surface Monitoring your organization will get notified whenever information has been found that can be used by malicious attackers to attack either your employees, partners or customers
Reduction in Attack Surface
By identifying and addressing forgotten, unused, outdated, or redundant assets, EASM tools empower organizations to strategically minimize their attack surface. Removing or diligently securing these assets decisively reduces potential exposure risks.
Visibility of Digital Assets
Edgewatch provide an inventory of an organization’s digital assets that are publicly accessible. This includes domains, subdomains, IP addresses, cloud assets, web applications, and more. This visibility ensures that organizations are aware of their entire external digital footprint.
Actionable Threat Intelligence
By having a continuous feed of information about the external attack surface, security teams can better correlate and analyze threat intelligence. This leads to improved incident response, as teams can better understand the context of threats and potential breaches.
Regulatory Compliance
Many industries and regions have regulations and standards that mandate specific security practices. Edgewatch can aid organizations in ensuring they meet these requirements by regularly auditing and reporting on their external security posture which allows having measurable metrics.
Edgewatch continuously automates hundreds of tests and probes to assess the breadth of your Attack Surface